Топология:
Пожалуйста, используйте следующую топологию для выполнения этого лабораторного упражнения:
Task 1:
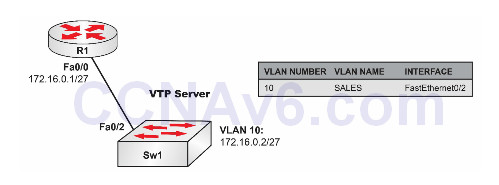
Настройте имена хостов на Sw1 и R1, как показано в топологии.
Task 2:
Создайте VLAN 10 на Sw1 и назначьте порт FastEthernet0/2 этой VLAN в качестве порта доступа.
Task 3:
Настройте IP-адрес 172.16.0.1/27 на интерфейсе R1 FastEthernet0/0 и IP-адрес 172.16.0.2/27 на интерфейсе Sw2 VLAN10. Убедитесь, что R1 может пинговать Sw1, и наоборот.
Task 4:
Настройте безопасность на порту FastEthernet0/2 на Sw1 таким образом, чтобы все MAC-адреса, полученные на этом интерфейсе, записывались в NVRAM коммутатора. NVRAM — это конфигурация запуска. Проверьте свою конфигурацию с помощью команд защиты портов в Cisco IOS.
Настройка и проверка
Task 1:
For reference information on configuring hostnames, please refer to earlier labs.
Task 2:
For reference information on configuring and verifying VLANs, please refer to earlier labs.
Task 3:
For reference information on configuring and verifying IP addresses, please refer to earlier labs.
Task 4:
Sw1#conf t
Enter configuration commands, one per line. End with CTRL/Z.
Sw1(config)#interface fastethernet0/2
Sw1(config-if)#switchport port-security
Sw1(config-if)#switchport port-security mac-address sticky
Sw1(config-if)#end
Sw1#
Sw1#copy startup-config running-config
Destination filename [running-config]?
2167 bytes copied in 2.092 secs (1036 bytes/sec)
Sw1#
Sw1#show port-security
Secure Port MaxSecureAddr CurrentAddr SecurityViolation Sec Action
(Count) (Count) (Count)
----------------------------------------------------------------------
Fa0/2 1 1 0 Shutdown
----------------------------------------------------------------------
Total Addresses in System : 1
Max Addresses limit in System : 1024
Sw1#show running-config interface fastethernet0/2
Building configuration...
Current configuration : 254 bytes
!
interface FastEthernet0/2
switchport port-security
switchport port-security mac-address sticky
switchport port-security mac-address sticky 0004.c058.5fc0
end
NOTE: When configuring port security, by default the learned MAC addresses are flushed when the switch is reloaded. To prevent this and ensure that the switch preserves MAC addresses that are dynamically learned via port security, you need to configure sticky learning. This configuration, in conjunction with the copy run start command, saves the learned MAC addresses to NVRAM. This means that when the switch is rebooted, the MAC addresses learned are not lost. The switch adds the switchport port-security mac-address sticky <mac-address> command dynamically under the interface for every sticky dynamically learned MAC address. So if 100 MAC addresses are learned this way, the switch would add 100 of these statements after the switchport port-security mac-address sticky command that you issued under the interface. Be very careful because this can create a very large configuration file in the real world!